Use Have I Been Pwned to Check Passwords in Active Directory
Have I Been Pwned is a site that was created by Troy Hunt. With this site, you can check if your email is one of the emails that have been in one or more known data breaches. You can get different info about what has been leaked. He also has SHA1 and NTLM hashes of all of the passwords that he has found in known data breaches and made them downloadable. This is what I will use to check passwords in a lab active directory I have. I will be using the NTLM hashes.
Prerequisites
- A virtual machine with a domain controller role installed.
- User accounts in the active directory that you can test against.
Install the PwnedPasswordDownloader
To download the NTLM hashes, go to Have I Been Pwned - Passwords. You will then be asked to go to the GitHub repository for the PwnedPasswordsDownloader. Follow the instructions to install the PwnedPasswordsDownloader and download the NTLM hashes to a file. I did find out that I needed to use parallelism when downloading, if not it would have taken me over an hour to download the file. I did use this command:
haveibeenpwned-downloader.exe -n pwnedpasswords_ntlm -p 256 -o
-n - ntlm hash
-p - parallelism
-o - overwrite file
Install DSInternals
Install DSInternals
Install-Module DSInternals -Force
Type y when you are asked to confirm the installation.
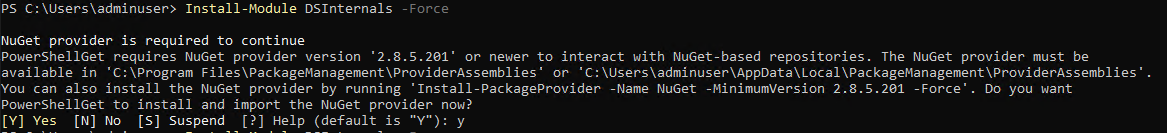
The test
Before I did this test, I created to test users:
test2with the password1234test3with the passwordsummer2023test4with a random generated 24-char password
Then I did run the command below:
$Domain = "DC=home,DC=local"
$Accounts = Get-ADReplAccount -All -Server dc-test -NamingContext $Domain # -Server <your server name>
$Results = $Accounts | Test-PasswordQuality -WeakPasswordHashesSortedFile .\pwnedpasswords_ntlm.txt >full_output.txt
$RiskyAccounts = $Accounts | where {$Results.WeakPassword -match $_.SamAccountName}
$RiskyAccounts | select SamAccountName,DisplayName,DistinguishedName | Export-Csv output.csv
In the output.csv file we can see that the test2 and test3 accounts are listed since both of the passwords used for the accounts are in the hashes from Have I Been Pawned. test4 is not on the list.:
#TYPE Selected.DSInternals.Common.Data.DSAccount
"SamAccountName","DisplayName","DistinguishedName"
"test2","test2 badpw","CN=test2 badpw,CN=Users,DC=home,DC=local"
"test3","test3 badpw2","CN=test3 badpw2,CN=Users,DC=home,DC=local"
If you change the third command in the commands I used earlier you can get some more information displayed to you:
$Accounts | Test-PasswordQuality -WeakPasswordHashesSortedFile .\pwnedpasswords_ntlm.txt
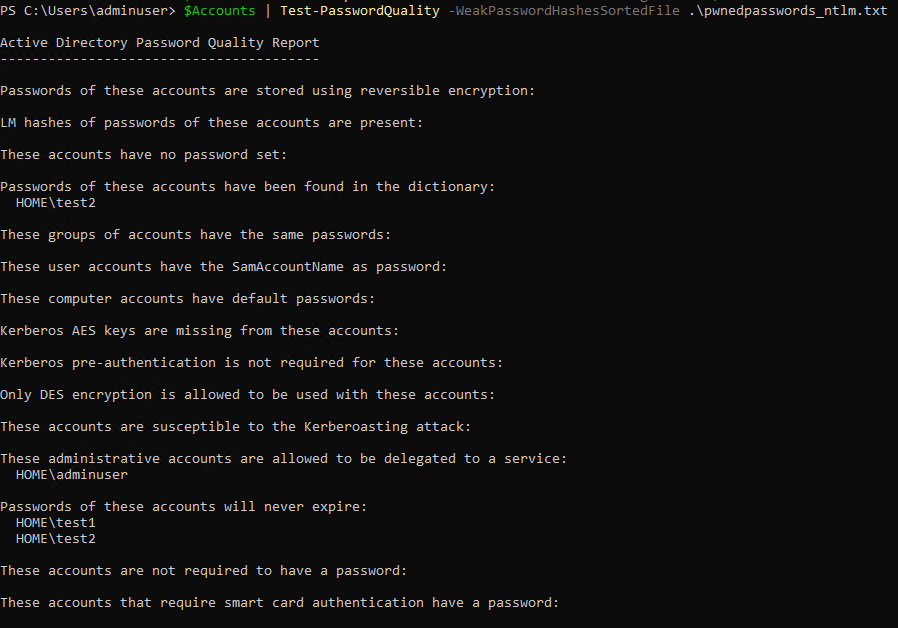 (Image does not show user test3, since I added the user after the first run to test with a couple of more passwords)
(Image does not show user test3, since I added the user after the first run to test with a couple of more passwords)
Update 29.03.2024
I installed the BadBlood repo from GitHub. I did this to test how long it would take to scan 2500 users. The first test I did, took only a couple of seconds since I had only added a couple of users to the domain. With 2500 users it took about 4 minutes to check all passwords.
Also modified the PowerShell command where I run the Test-PasswordQuality command to create a full output since it gives some other information besides just bad passwords.