Cowrie Honeypot
This was originally a weekend project, but that become a project that I did sink some hours into. Originally I was playing around with Terraform in Azure since I wanted to learn about it. And since I had a virtual machine running, why not use it for something interesting? Data was collected from 12:22 29.01.2023 (UTC) to 08:30 04.02.2023 (UTC).
Setup/configuration
Sources used during the setup/configuration:
https://medium.com/threatpunter/how-to-setup-cowrie-an-ssh-honeypot-535a68832e4c
https://cowrie.readthedocs.io/en/latest/INSTALL.html
https://github.com/cowrie/cowrie
First I did create a virtual machine in Azure using Terraform. The template can be found at: https://github.com/rhofset/Templates/tree/main/Terraform/Azure/Linux%20Virtual%20Machine
Connect to the created machine
ssh -i C:\Users\<USER>\.ssh\<SSHKEY> <USERNAME>@<IP_ADDRESS>
Change port for SSH
# change to port 9999:
sudo nano /etc/ssh/sshd_config
sudo service ssh restart
# Connect from my local machine using the new port:
ssh -i C:\Users\<USER>\.ssh\<SSHKEY> <USERNAME>@<IP_ADDRESS> -p 9999
Update and install packages
sudo apt update
sudo apt install git python3-virtualenv libssl-dev libffi-dev build-essential libpython3-dev python3-minimal authbind virtualenv
sudo apt install python3.10-venv
sudo apt upgrade
Got some problems creating the virtual environment later in the text, so needed to add the python3.10-venv.
Add Cowrie user
# Add user:
sudo adduser --disabled-password cowrie
# Change user:
sudo su - cowrie
Clone repository
# Git clone
git clone http://github.com/cowrie/cowrie
# Goto folder
cd cowrie
Activate virtual environment
# Create env
python3 -m venv cowrie-env
# Activate enc
source cowrie-env/bin/activate
# Install packages:
python3 -m pip install --upgrade pip
python3 -m pip install --upgrade -r requirements.txt
Redirect port 22 to 2222
sudo iptables -t nat -A PREROUTING -p tcp --dport 22 -j REDIRECT --to-port 2222
Another solution here is to get Cowrie to listen on port 22.
Start
./bin/cowrie start
Stop
./bin/cowrie stop
Result
In total there were 8815 login attempts. 5379 failed and 3436 was successful. All of the result under is carved out from the logfiles using Power Bi Desktop. The default username/password DB was used for allowing logins to the honeypot.
# Default username/password:
root:x:!root
root:x:!123456
root:x:!/honeypot/i
root:x:*
tomcat:x:*
oracle:x:*
*:x:somepassword
*:x:*
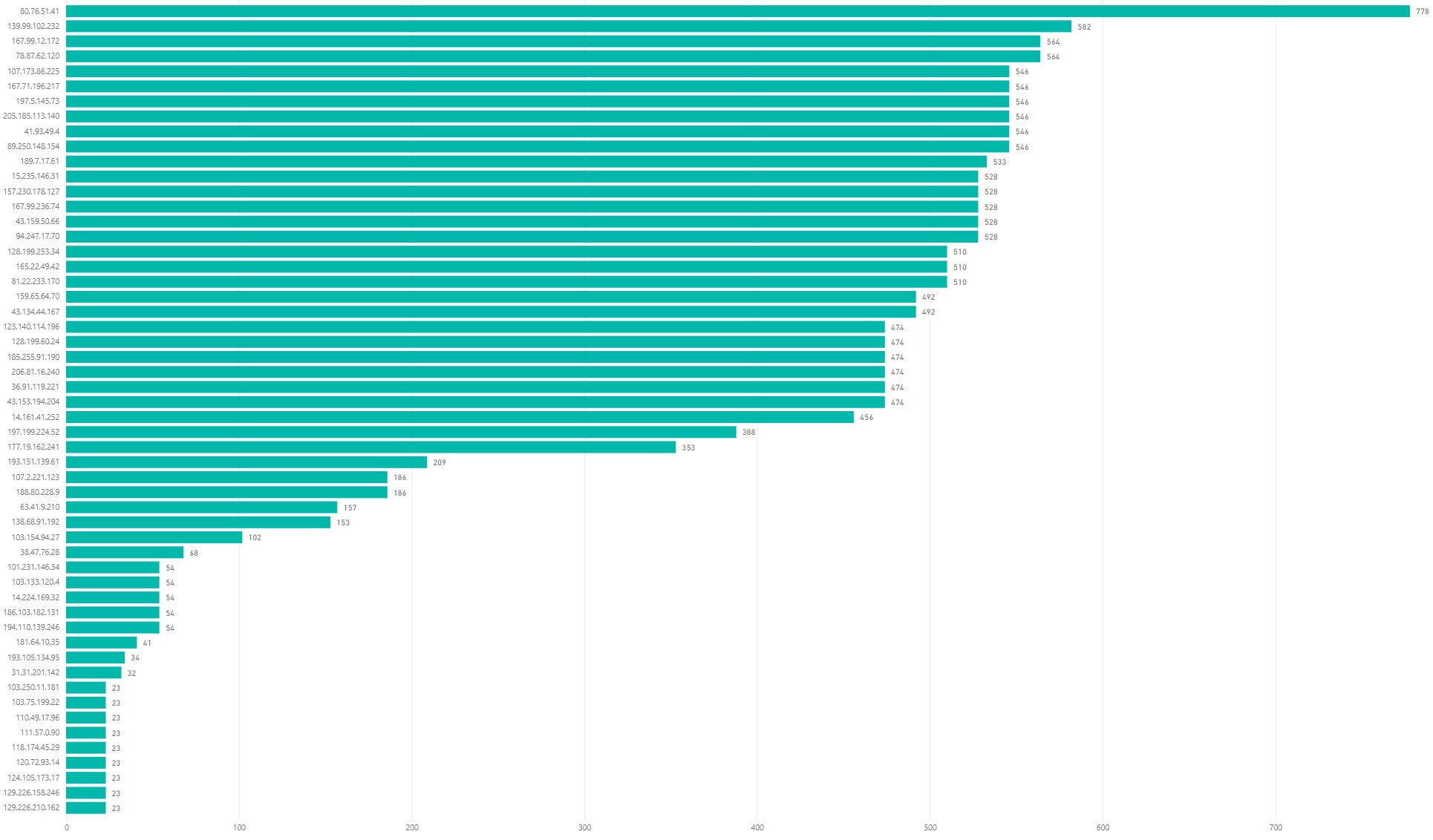
IP’s
Username
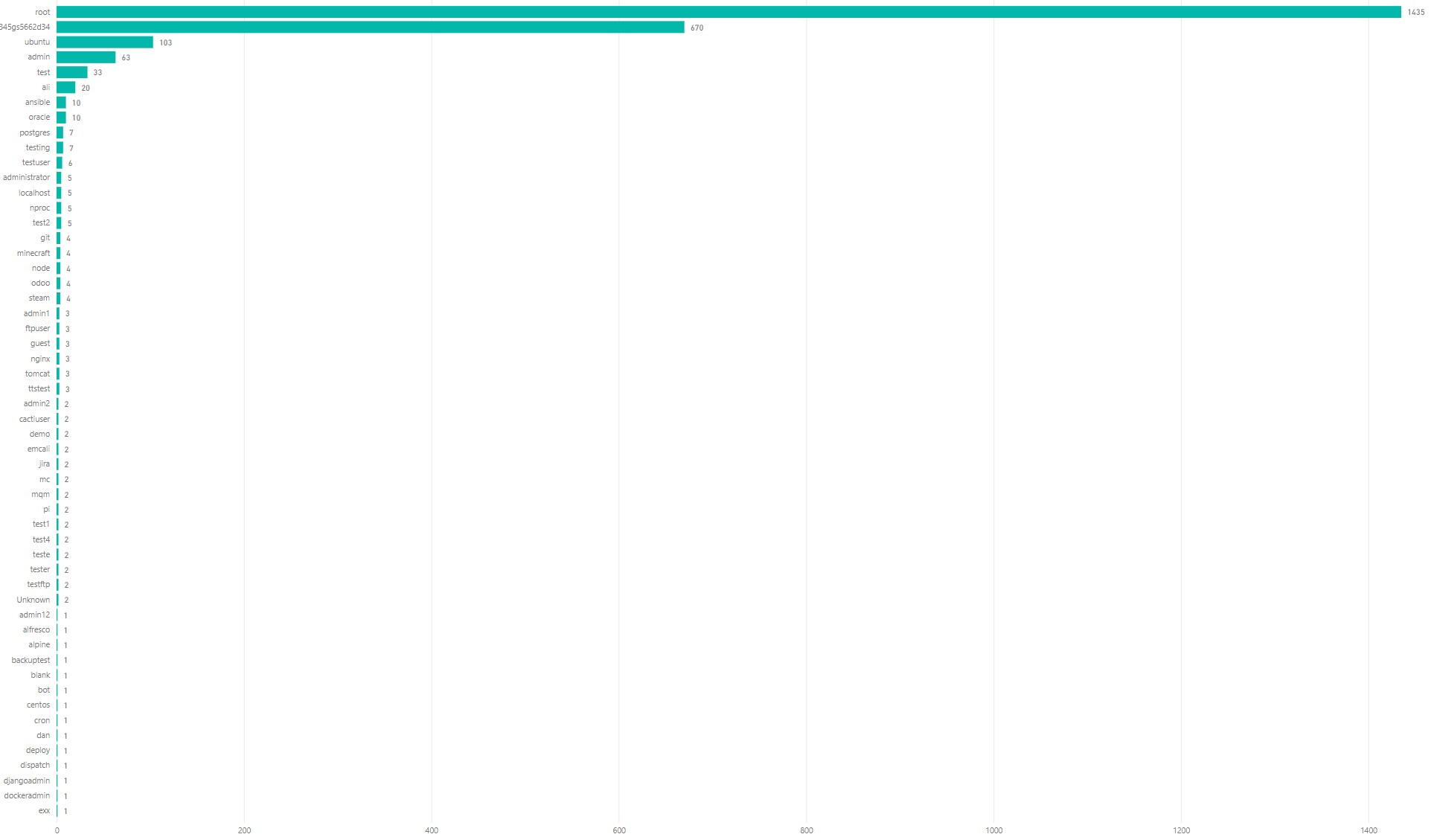
I have removed all attempts where an empty username is used (“null”). I have no idea what device or service that has “345gs5662d34” as a username.
Password
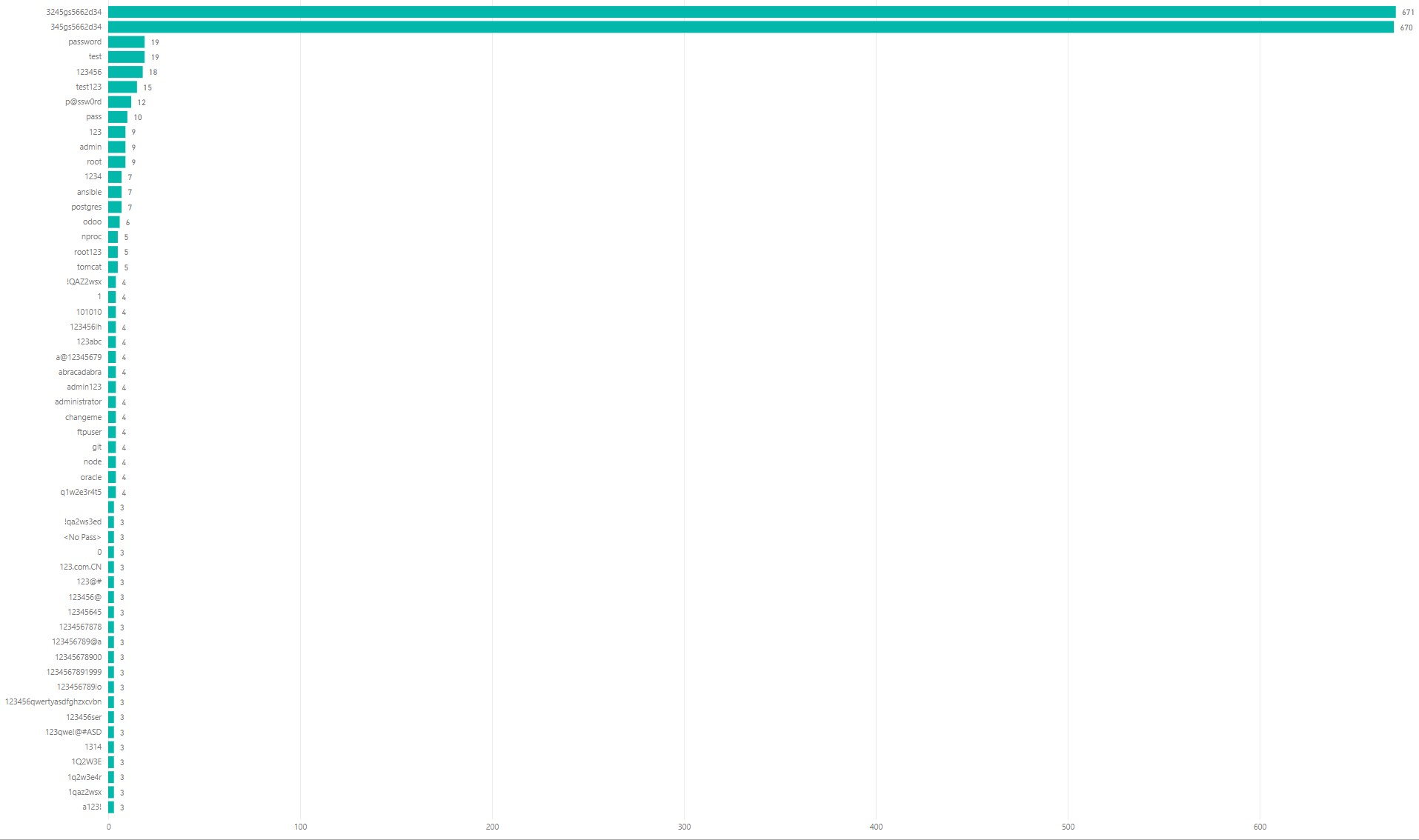
For the password results, I have done the same as for the usernames and removed “null” from the list. I have also no idea what the two passwords at the top of the list are used for (3245gs5662d34 and 345gs5662d34). Since there are many attempts to use them, I would think they are some default passwords for a service or device. Let me know if anyone knows.
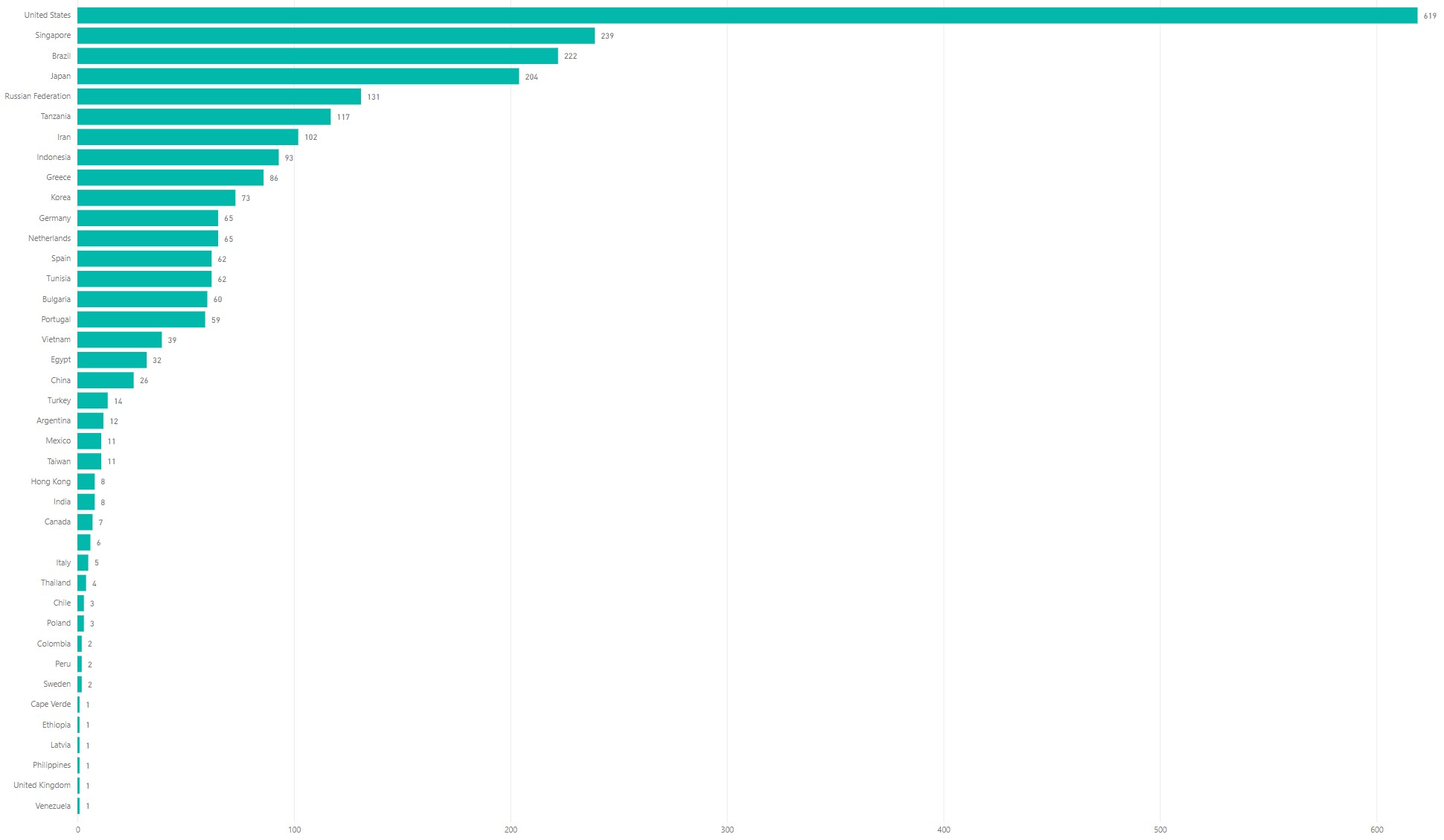
Country
Login attempts per day
Total login attempts:
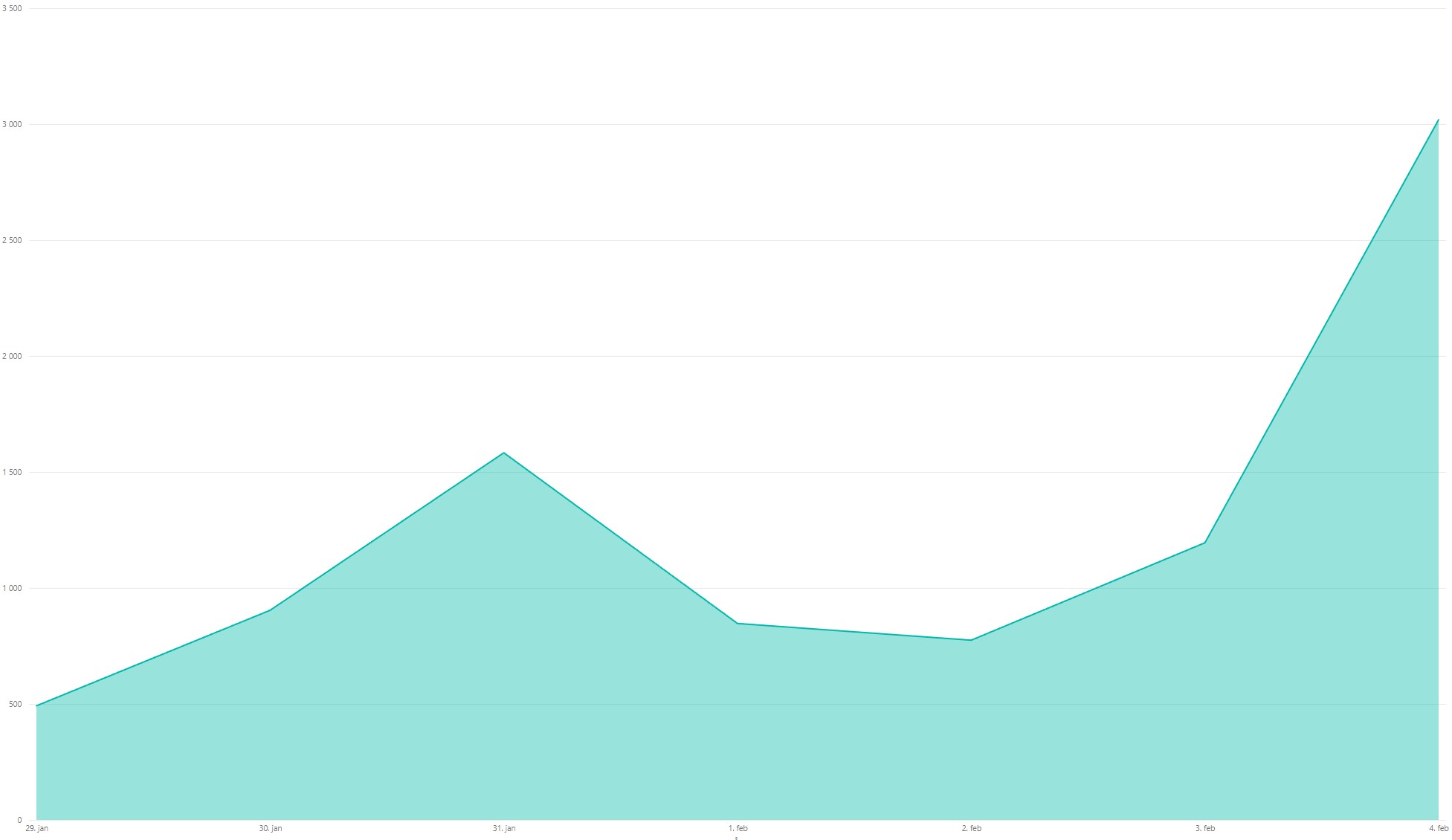
Total login attempts succeed:
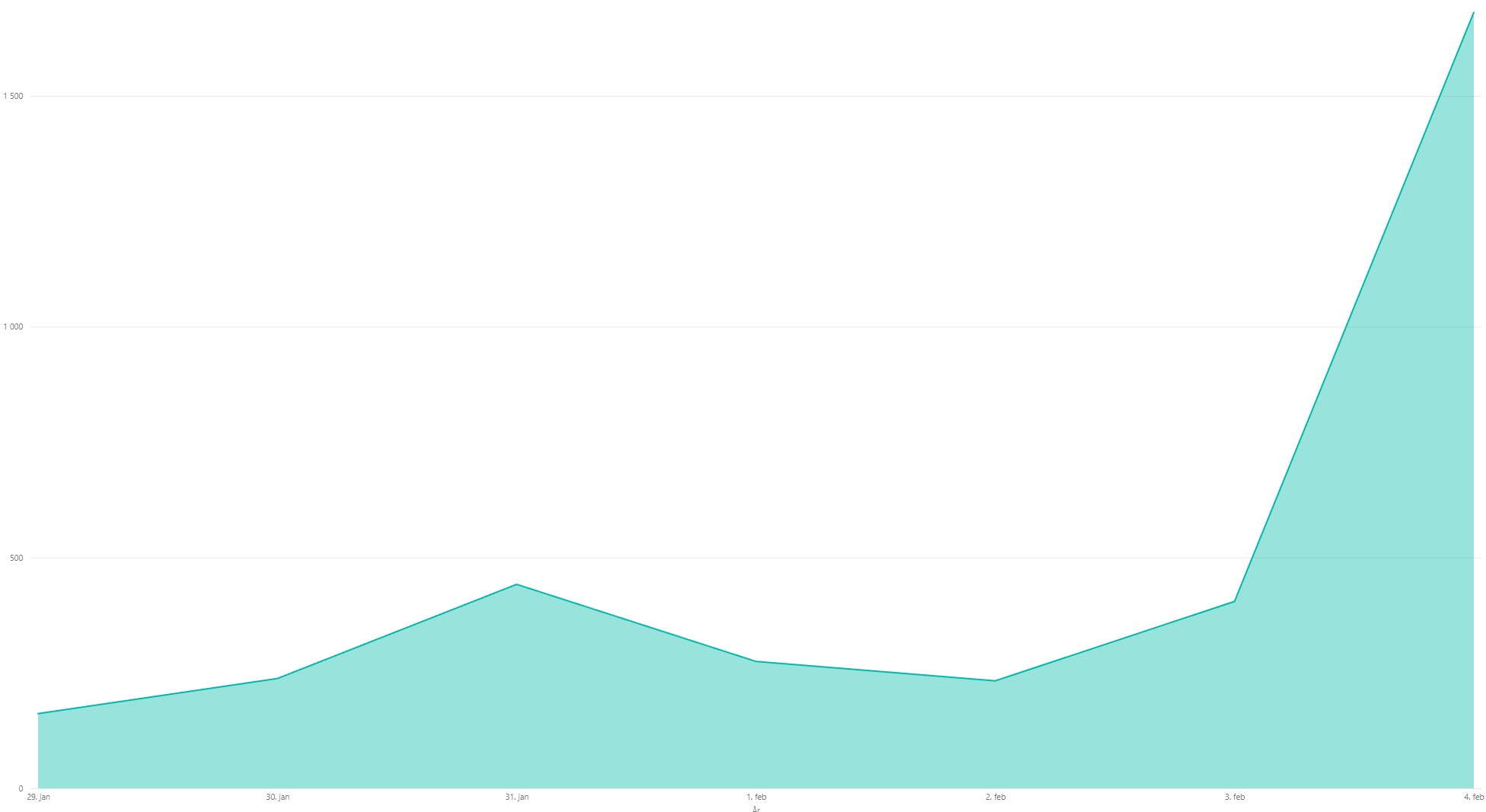
Total login attempts failed:
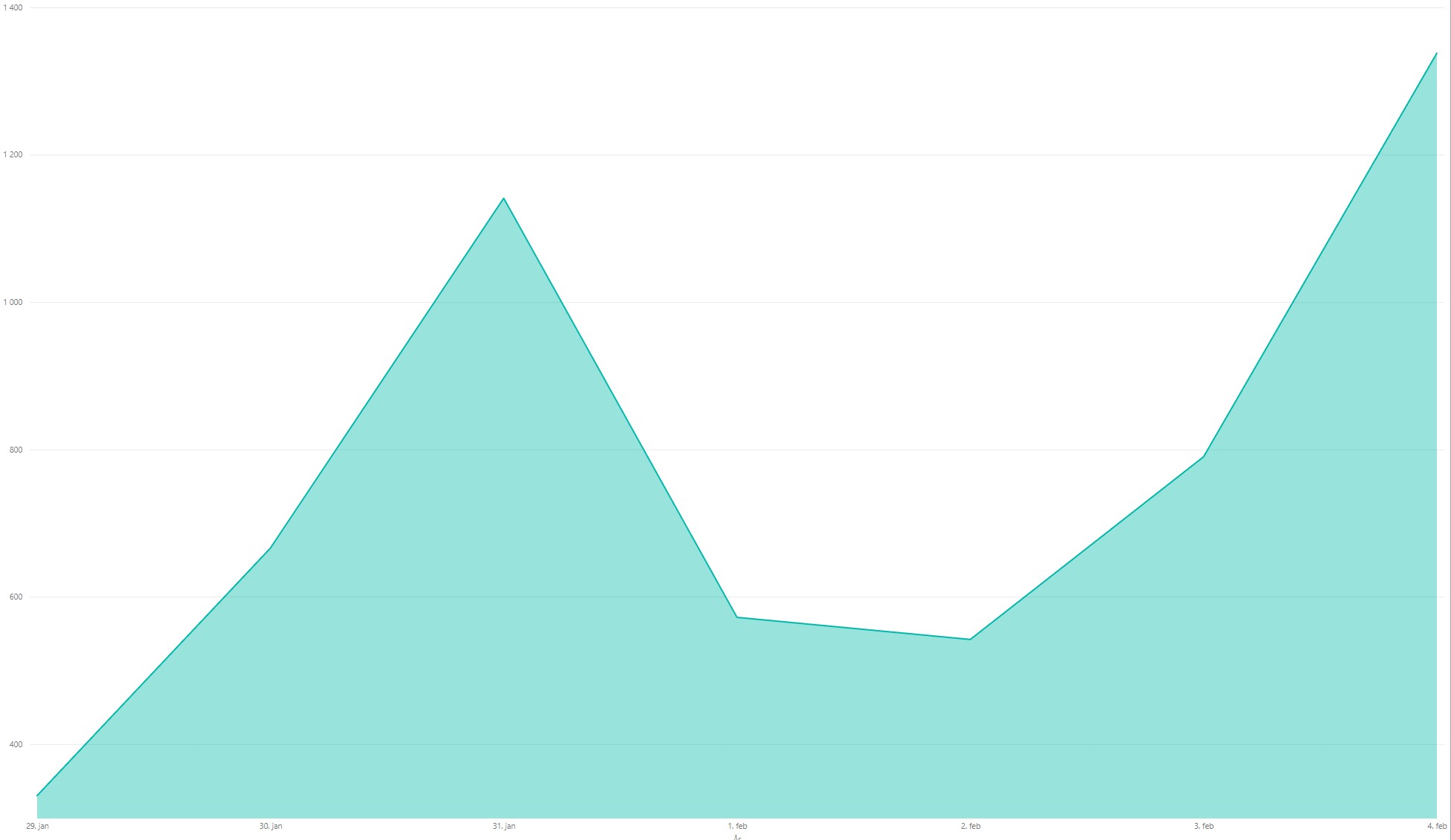
Files uploaded
Hashes from files that were uploaded to the honeypot while it was active. I forgot to save and transfer the files that were uploaded before I shut down and destroyed the virtual machine in Azure. It was stupid since there were samples that were not uploaded to Virustotal.
| Hash | Size | Virustotal detection |
|---|---|---|
| 01ba4719c80b6fe911b091a7c05124b64eeece964e09c058ef8f9805daca546b | 1B | 0/60 |
| 0815320fe446ceedbc2ad4953d068111a795b087d994d145147452a970dde59d | 174B | 20/60 |
| 771229b5b05e22d4f43e728b38c1e6f08fe7157e3c6dcade0e9af065f710f22d | 64,91KB | 37/63 |
| 942641e3997f98bd38ad91561f50910b071a9c495fdff745996cd6c0c2212c18 | 765B | 0/60 |
| a8460f446be540410004b1a8db4083773fa46f7fe76fa84219c93daa1669f8f2 | 389KB | 12/59 |
| c5bd2146ebbe575a47a666e07b99eb526d46d74e0d7758bf0bf5cb5b3adaa55a | 53,25KB | 44/63 |
| cdf16795ec6ea3857851ece799fbe687e0b646a3f555ebd34199a64500b705eb | 83,79KB | 37/63 |
| e4b85b229c320be8df7fdb02d16a7ebe9aef649c82f2f5750488744a39298f72 | ? | Not found |
| ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73 | ? | Not found |
| f06d698967cee77e5a7bf9835b0a93394097e7590c156ed0d8c6304345701cfa | 3,65MB | 34/62 |
Log files
If anybody wants the log files, let me know.
Lesson learned
If I do this one more time, I think I will implement a log analysing tool to the honeypot, like Azure Sentinel, Kibana/Elasticstack or something similar.